Reuse ASUS P9X79 DELUXE motherboard
CPU
ASUS Info
P9X79 DELUXE
Following CPUs are supported
Core i7-3820 (3.6G,L3:10M,4C,HT,rev.M0)
Core i7-3820 (3.6G,L3:10M,4C,HT,rev.M1)
Core i7-3930K (3.2G,L3:12M,6C,HT,rev.C1)
Core i7-3930K (3.2G,L3:12M,6C,HT,rev.C2)
Core i7-3960X Extreme Edition(3.3G,L3:15M,6C,HT,rev.C1)
Core i7-3960X Extreme Edition(3.3G,L3:15M,6C,HT,rev.C2)
Core i7-3970X Extreme Edition(3.5G,L3:15M,6C,HT,150W,rev.C2)
Core i7-4820K (3.7GHz, L3:10M, 4C, HT, 130W, rev.S1)
Core i7-4930K (3.4GHz, L3:12M, 6C, HT, 130W, rev.S1)
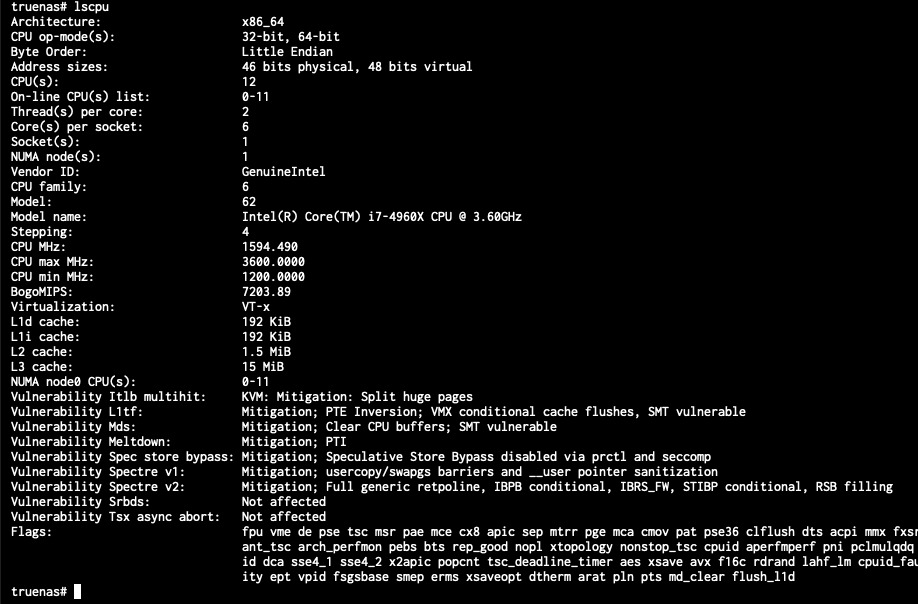
Core i7-4960X (3.6G, L3:15M, 6C, HT, 130W, rev.S1)
Following CPUs are partially supported as description below
Intel Xeon Processor Family is designed for servers. Some features may not support when installed on X79 series chipsets. For more details, refer to ASUS support site at http://support.asus.com.
Intel Xeon E5-1620 v2 (3.7G,130W,L3:10M,4C,HT)
Intel Xeon E5-1650 v2 (3.5G,130W,L3:12M,6C,HT)
Intel Xeon E5-1660 v2 (3.7G,130W,L3:15M,6C,HT)
Intel Xeon E5-2603 v2 (1.8G,80W,L3:10M,4C,HT)
Intel Xeon E5-2609 v2 (2.5G,80W,L3:10M,4C,HT)
Intel Xeon E5-2620 v2 (2.1G,80W,L3:15M,6C,HT)
Intel Xeon E5-2630 v2 (2.6G,80W,L3:15M,6C,HT)
Intel Xeon E5-2630L v2 (2.4G,60W,L3:15M,6C,HT)
Intel Xeon E5-2637 v2 (3.5G,130W,L3:15M,4C,HT)
Intel Xeon E5-2640 v2 (2.0G,95W,L3:20M,8C,HT)
Intel Xeon E5-2643 v2 (3.5G,130W,L3:25M,6C,HT)
Intel Xeon E5-2650 v2 (2.6G,95W,L3:20M,8C,HT)
Intel Xeon E5-2650L v2 (1.7G,70W,L3:25M,10C,HT)
Intel Xeon E5-2660 v2 (2.2G,95W,L3:25M,10C,HT)
Intel Xeon E5-2667 v2 (3.3G,130W,L3:25M,8C,HT)
Intel Xeon E5-2670 v2 (2.5G,115W,L3:25M,10C,HT)
Intel Xeon E5-2680 v2 (2.8G,115W,L3:25M,10C,HT)
Intel Xeon E5-2687W v2 (3.4G,150W,L3:20M,8C,HT)
Intel Xeon E5-2690 v2 (3.0G,130W,L3:25M,10C,HT)
Intel Xeon E5-2695 v2 (2.4G,115W,L3:30M,12C,HT)
Intel Xeon E5-2697 v2 (2.7G,130W,L3:30M,12C,HT)
Intel Info
Compatibility for FCLGA2011, FCLGA2011-v3, and FCLGA2066 Sockets (Intel® Core™ X-series Processors)
FCLGA2011 socket compatibility
These processors are compatible with the FCLGA2011 socket. They are backward and forward compatible with the motherboard supporting FCLGA2011 socket. We recommend you always download the latest BIOS from the motherboard vendor when installing a new processor. For any issues, please check with your board manufacturer to see if your board is compatible with the processor you intend to use.
Intel® Core™ i7-4960X Processor Extreme Edition
Intel® Core™ i7-4930K / i7-4820K Processors
Intel® Core™ i7-3960X / i7-3970X Processor Extreme Edition
Intel® Core™ i7-3930K / i7-3820 Processors
Memory
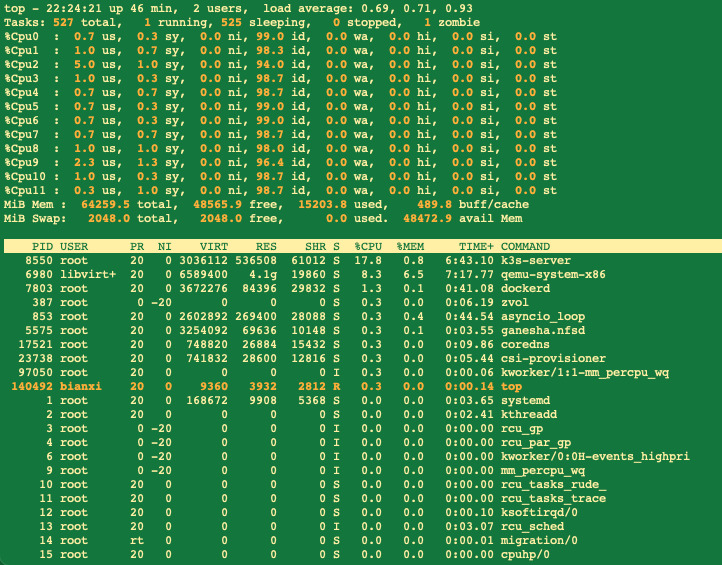
CORSAIR Vengeance 32GB (4 x 8GB) 240-Pin DDR3 SDRAM DDR3 1600 (PC3 12800) Desktop Memory Model CMZ32GX3M4X1600C10
Final result
CPU Info
Memory
References
P9X79 DELUXE

